

AZ302 – Securing HTTP Triggers with Azure AD (Logic app, Power Automate)
Note – I am using Azure logic app in this article
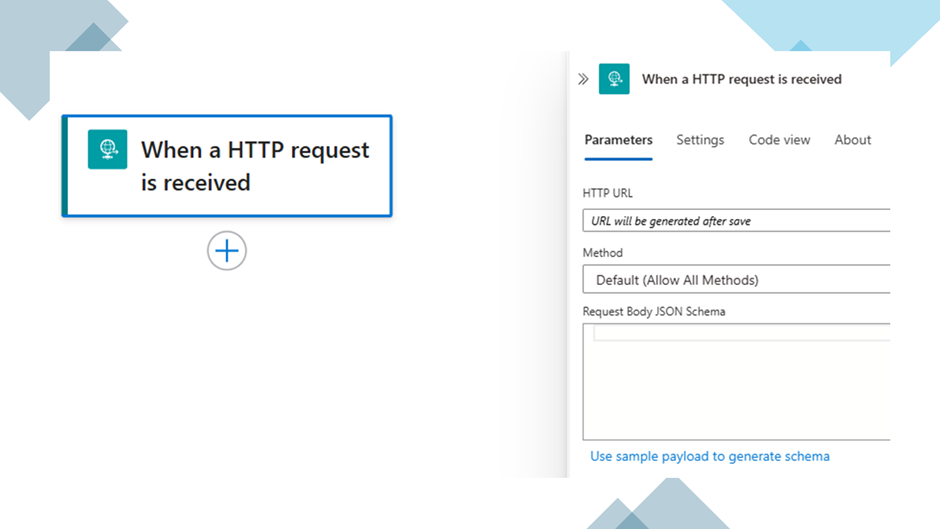
Table of Contents
ToggleIntroduction
By default, Azure Logic Apps using HTTP triggers are secured with a Shared Access Signature (SAS) token. While SAS tokens provide basic security, they also have risks. A more secure approach is to use Azure Active Directory (Azure AD) authentication. This article explains why and how to configure an Azure Consumption-based Logic App to require bearer token authentication via Azure AD.
Why Move from SAS Tokens to Azure AD Authentication?
Understanding SAS Tokens
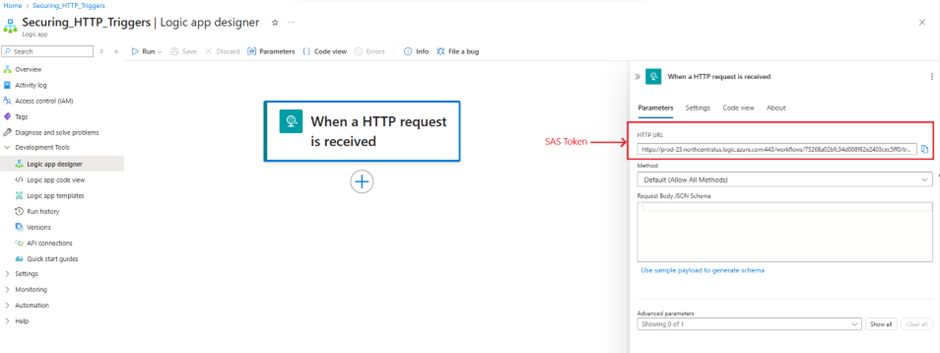
- SAS tokens are included in the URL of an HTTP-triggered Logic App request. They grant access to the Logic App without requiring authentication.
Breakdown of above SAS URL
| Component | Value |
| Scheme | https |
| Netloc | prod-23.northcentralus.logic.azure.com:443 |
| Path | /workflows/75268a02bfc34d008f62e2403cec5ff0/triggers/When_a_HTTP_request_is_received/paths/invoke |
| Query Parameters | |
| api-version | 2016-10-01 |
| sp | /triggers/When_a_HTTP_request_is_received/run |
| sv | 1.0 |
| sig | heDicGBqdJzY0lBGeK3NjoZCj6aPQ10NtlC2M_ryeGw |
Security Risks of SAS Tokens
- Exposed in URLs: If someone gains access to the URL, they can trigger the Logic App.
- No Expiry by Default: SAS tokens do not expire unless specifically regenerated.
- Lack of Governance Controls: Unlike Azure AD, SAS tokens do not support Conditional Access, MFA, or Role-Based Access Control (RBAC).
By integrating Azure AD authentication, we enhance security with token expiration, role-based access control, and conditional access policies.
Step-by-Step: Configuring Azure AD Authentication for Logic App
Step 1: Test the Logic App with a SAS Token
💡 Why? This ensures that the Logic App is functioning before implementing Azure AD authentication.
Before making any changes, confirm that the Logic App is accessible via SAS authentication:
- Add Response action in Logic app

- Open Postman.
- Send a POST request to the Logic App’s HTTP trigger URL (including the SAS token).
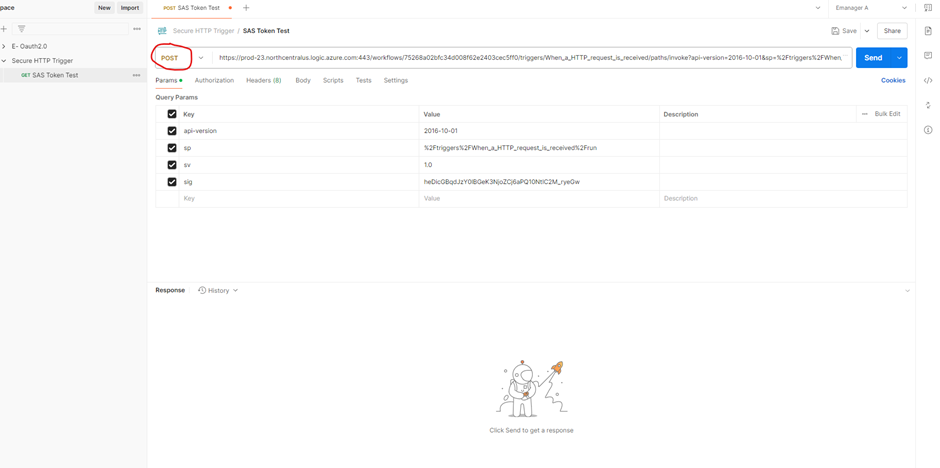
- If a response is received, SAS authentication is working.
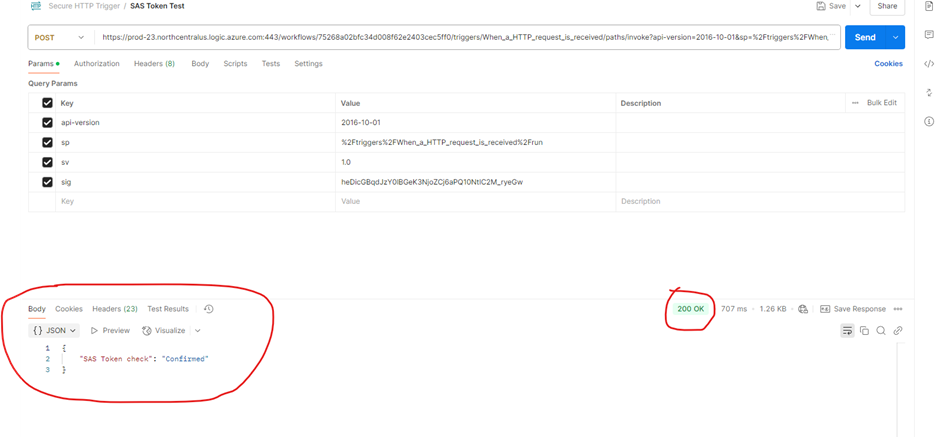
Step 2: Set Up Azure AD Authorization
To use Azure AD authentication, we need to create two Azure AD applications:
- Client App – Represents the system calling the Logic App.
- Service App – Represents the Logic App itself.
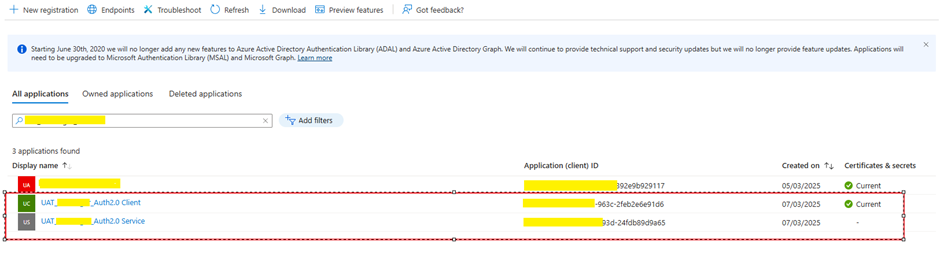
1. Register Azure AD App – Client
This application will request a bearer token to trigger the Logic App.
- In Azure AD, create a new app registration (Client App).
- Note Client ID and Tenant ID.
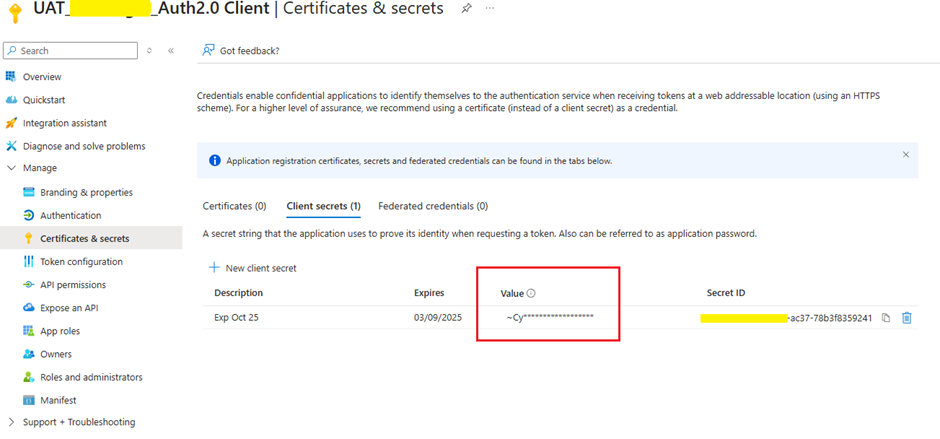
- Generate a Client Secret (this will be used to authenticate requests).
2. Register Azure AD App – Service
This application acts as the protected API (Logic App).
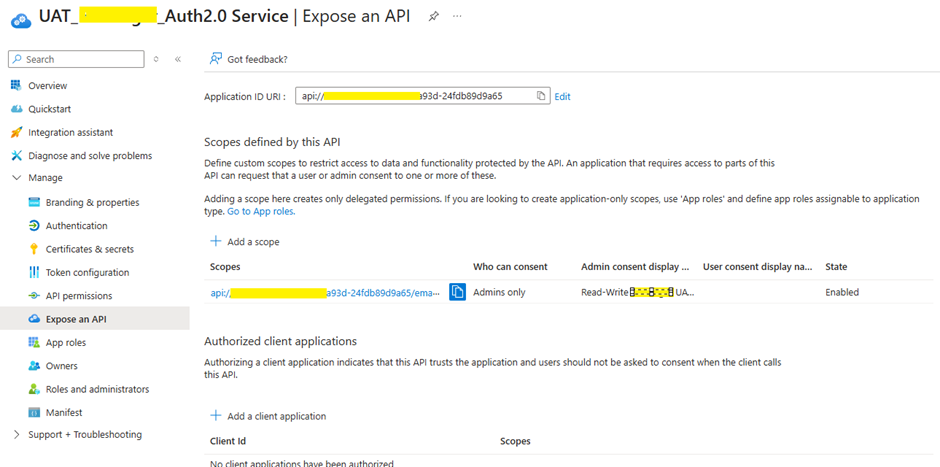
- Create a new app registration (Service App).
- Add an App ID URI (e.g., api://mylogicapp).
- Define API Scope:
- Example: api://mylogicapp/.default
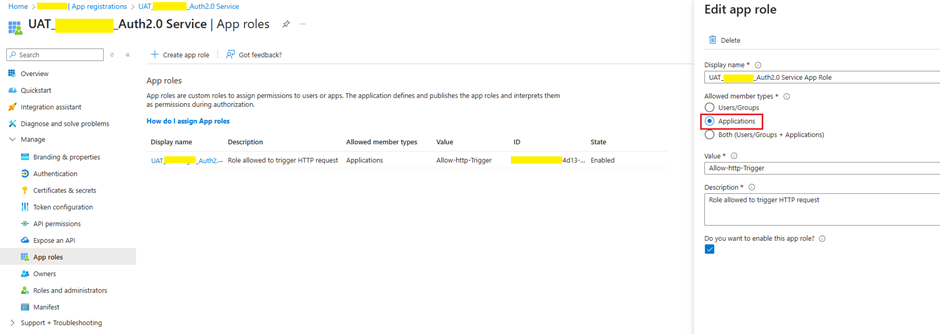
- Create an App Role:
- Assign an “Application” member type role.
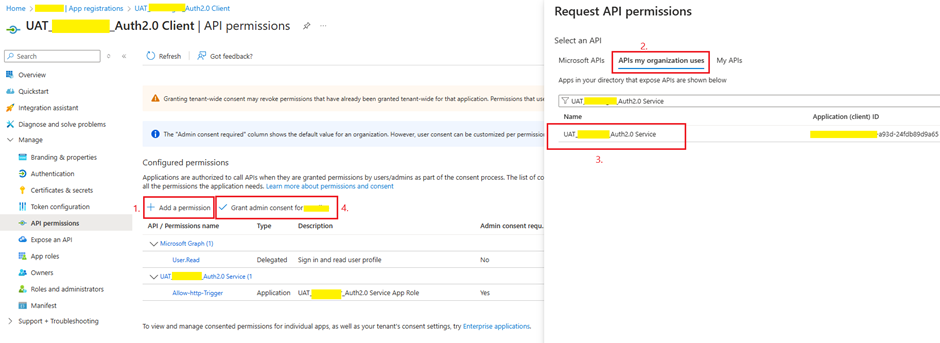
3. Grant Permissions
- In the Client App, grant permission to the Service App’s API scope.
- Grant Admin Consent for these permissions.
💡 Why? Without proper permissions, the Client App cannot obtain a valid access token.
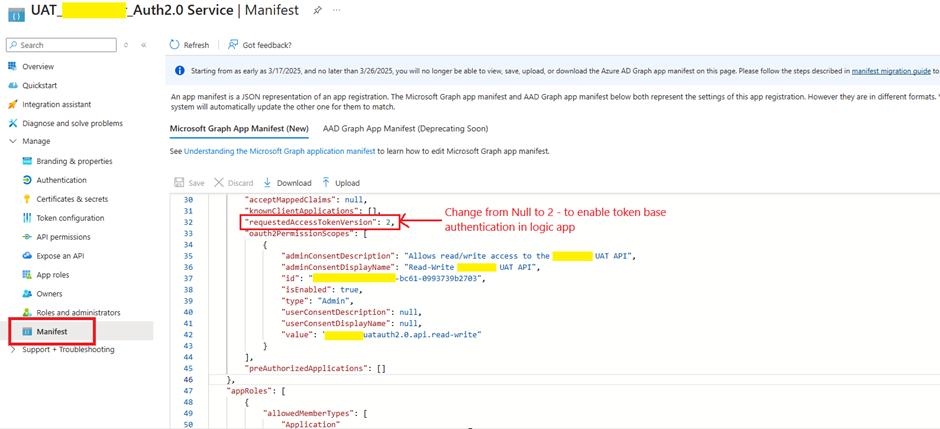
4. Modify Azure AD App Service Manifest
- Open the Service App’s manifest file in Azure AD.
- Change requestedAccessTokenVersion from null to 2.
💡 Why? This enables token-based authentication in the Logic App.
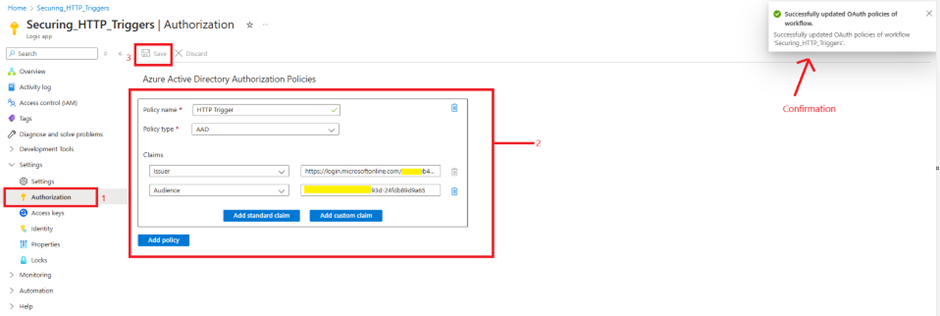
Step 3: Configure Authorization Policy in Logic App
- Open the Logic App in Azure.
- Navigate to Authorization Policy and create a new policy:
- Issuer: https://login.microsoftonline.com/{tenantid}/v2.0
- Audience: Client ID of the Service App.
- Save the policy.
💡 Why? This policy enforces that only Azure AD-authenticated requests are allowed.
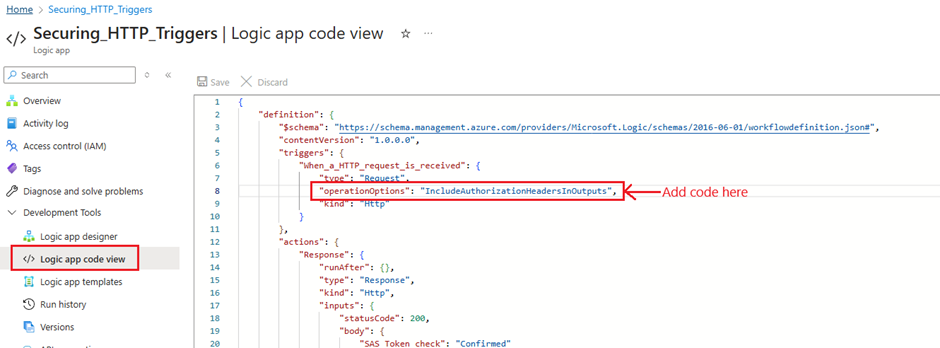
Step 4: Modify Logic App Code
- Open the Logic App’s code view.
- Add the following property:
"operationOptions": "IncludeAuthorizationHeadersInOutputs"💡 Why? This ensures the authorization headers are included in the Logic App execution logs.
Step 5: Test with Bearer Token
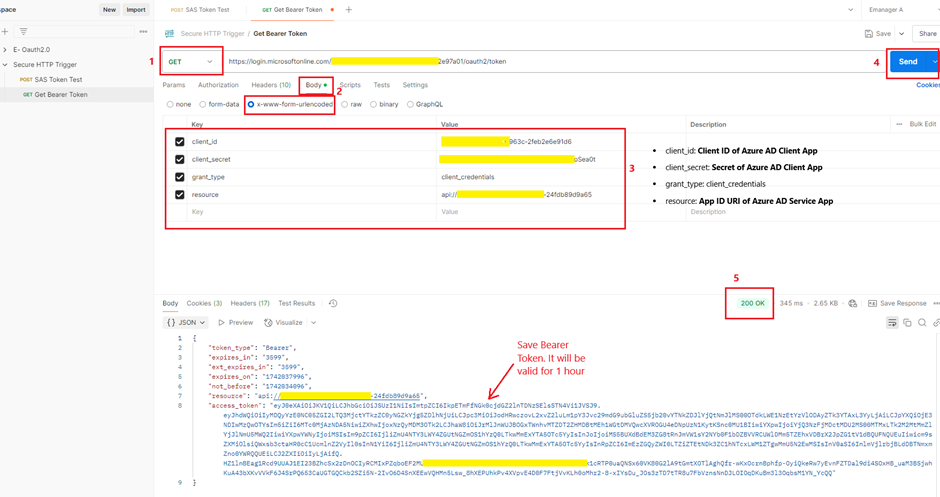
1. Get a Bearer Token via Postman
- Make a POST request to:
https://login.microsoftonline.com/{tenantid}/oauth2/token- Set Body parameters (x-www-form-urlencoded):
- client_id: Client ID of Azure AD Client App
- client_secret: Secret of Azure AD Client App
- grant_type: client_credentials
- resource: App ID URI of Azure AD Service App
- Copy the access token from the response.
💡 Why? This step verifies that the Client App can authenticate with Azure AD.
2. Trigger Logic App Using Bearer Token
- In Postman, send a POST request to the Logic App URL without the SAS token.
- Under Authorization, choose Bearer Token and paste the token.
- Click Send.
💡 Why? If the request succeeds, Azure AD authentication is working!
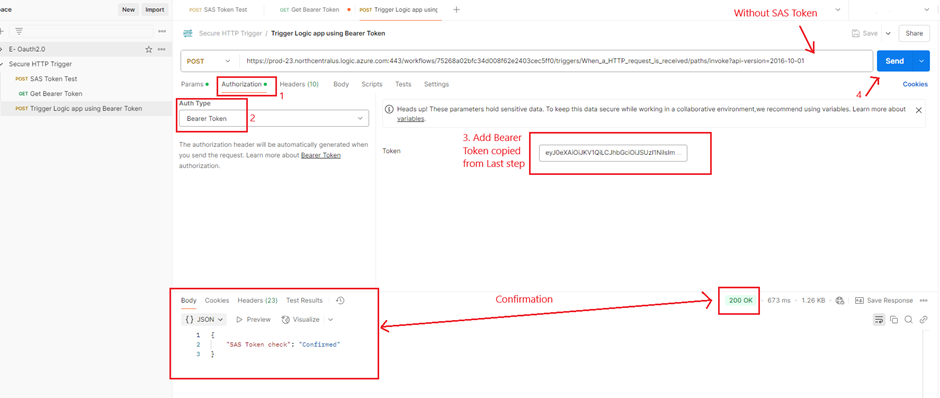
Confirmation of Logic app trigger

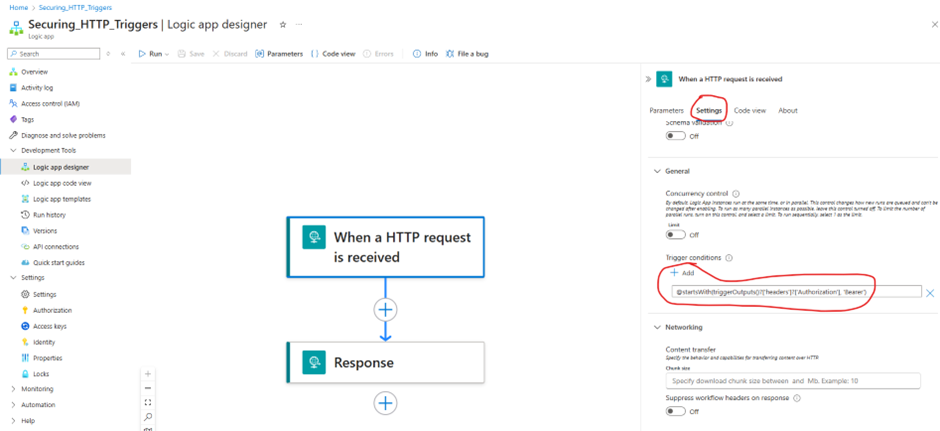
Step 6: Restrict Logic App to Require Bearer Token
Note – at this stage, the SAS token is still capable of triggering the logic app. If you rerun step 1, the logic app will be activated.
To block SAS token requests, add a trigger condition:
@startsWith(triggerOutputs()?['headers']?['Authorization'], 'Bearer')💡 Why? This ensures the Logic App only accepts bearer token authentication and blocks unauthorized access.
Step 7: Test SAS Token
- SAS Token failed due to SAS token are acceptable by logic app
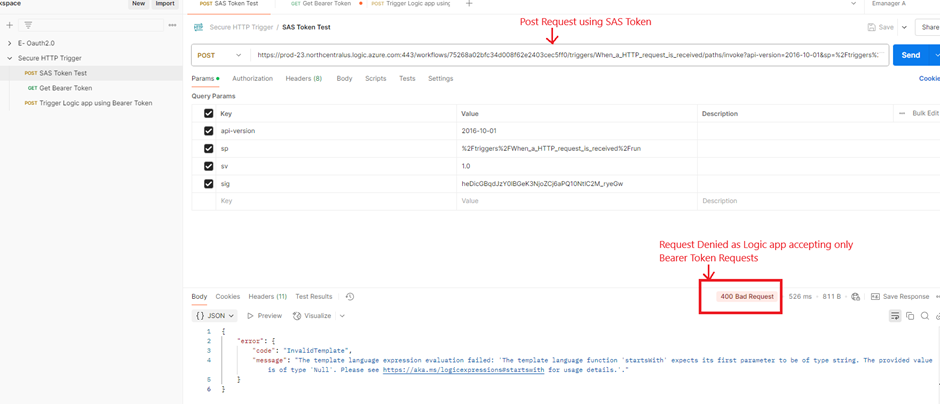
Note – The logic app does not retain history because there is no trigger.
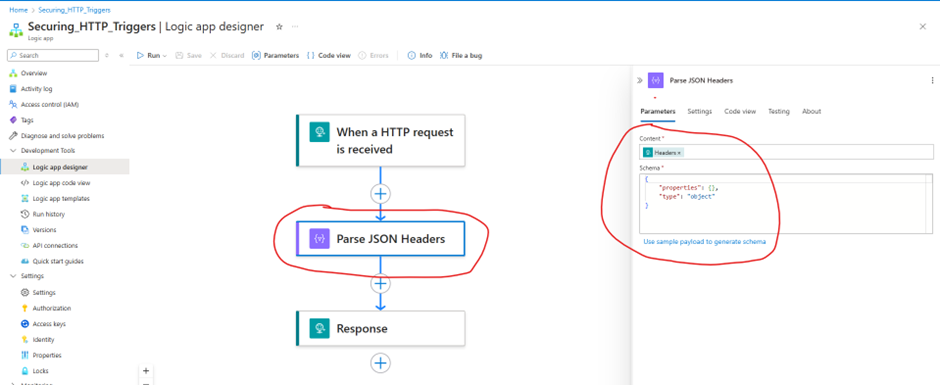
Step 8: Capture Bearer Token in Logic App Execution (Error Handling)
- At this stage, the logic app only accepts triggers with a Bearer token header. The logic app validates the Bearer token upon triggering
- Add a Parse JSON action to extract the bearer token from request headers.
💡 Why? This allows logging and further validation of incoming requests.
Test
- Send Request using Bearer token (Correct Bearer Token)
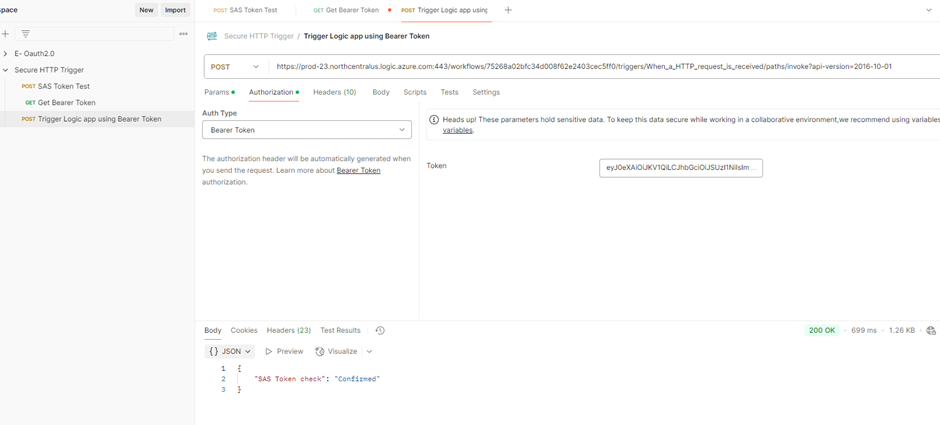
- The Bearer token was captured, and since it was a valid token, the logic app run was successful.

- Send Request using Bearer token (InCorrect Bearer Token)
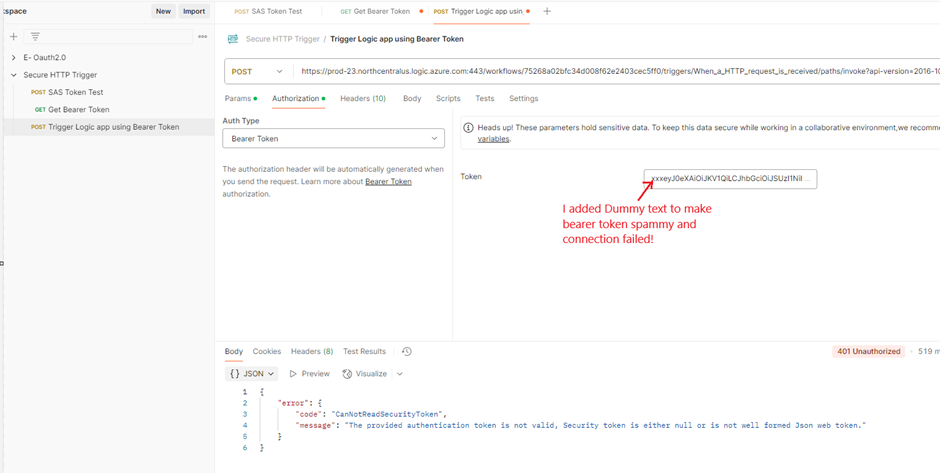
Logic app also not triggered
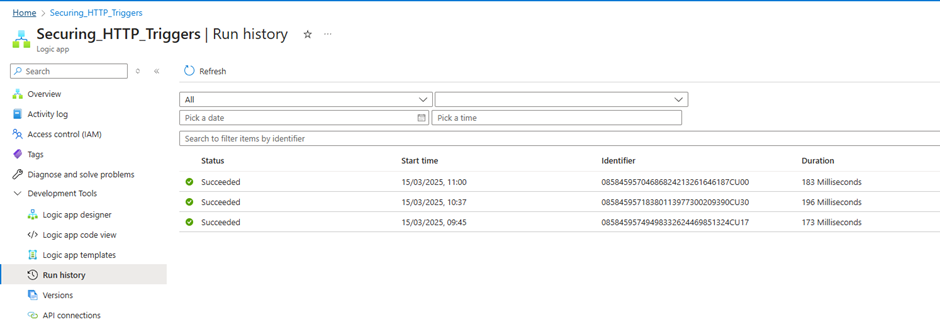
Logic app is now secured and cannot be triggered without legit Bearer token 😊
Final Thoughts
By following these steps, we:
✅ Removed reliance on SAS tokens, eliminating URL-based security risks.
✅ Implemented Azure AD authentication, enabling token expiration, role-based access, and governance controls.
✅ Ensured only valid bearer tokens can trigger the Logic App, enhancing security.
This setup significantly improves the security posture of Azure Logic Apps while integrating seamlessly with Azure AD’s identity and access management capabilities. 🚀
Expand Your Knowledge: See More Azure Blogs
I am Yogeshkumar Patel, a Microsoft Certified Solution Architect and Enterprise Systems Manager with deep expertise across Dynamics 365 Finance & Supply Chain, Power Platform, Azure, and AI engineering. With over six years of experience, I have led enterprise-scale ERP implementations, AI-driven and agent-enabled automation initiatives, and secure cloud transformations that optimise business operations and decision-making. Holding a Master’s degree from the University of Bedfordshire, I specialise in integrating AI and agentic systems into core business processes streamlining supply chains, automating complex workflows, and enhancing insight-driven decisions through Power BI, orchestration frameworks, and governed AI architectures. Passionate about practical innovation and knowledge sharing, I created AIpowered365 to help businesses and professionals move beyond experimentation and adopt real-world, enterprise-ready AI and agent-driven solutions as part of their digital transformation journey. 📩 Let’s Connect: LinkedIn | Email 🚀
















Post Comment