
PUR502 – Building a Data-Centric Security Model in Microsoft 365
Table of Contents
ToggleIntroduction
For years, cybersecurity focused on keeping attackers out of the network.
But in today’s world of hybrid work, cloud apps, and AI-driven workflows, the network perimeter has dissolved. The only constant is data , where it resides, how it moves, and who uses it.
That’s why leading organizations are adopting a data-centric security model.
Instead of guarding borders, they guard information itself , applying protection that travels with data across devices, clouds, and AI tools.
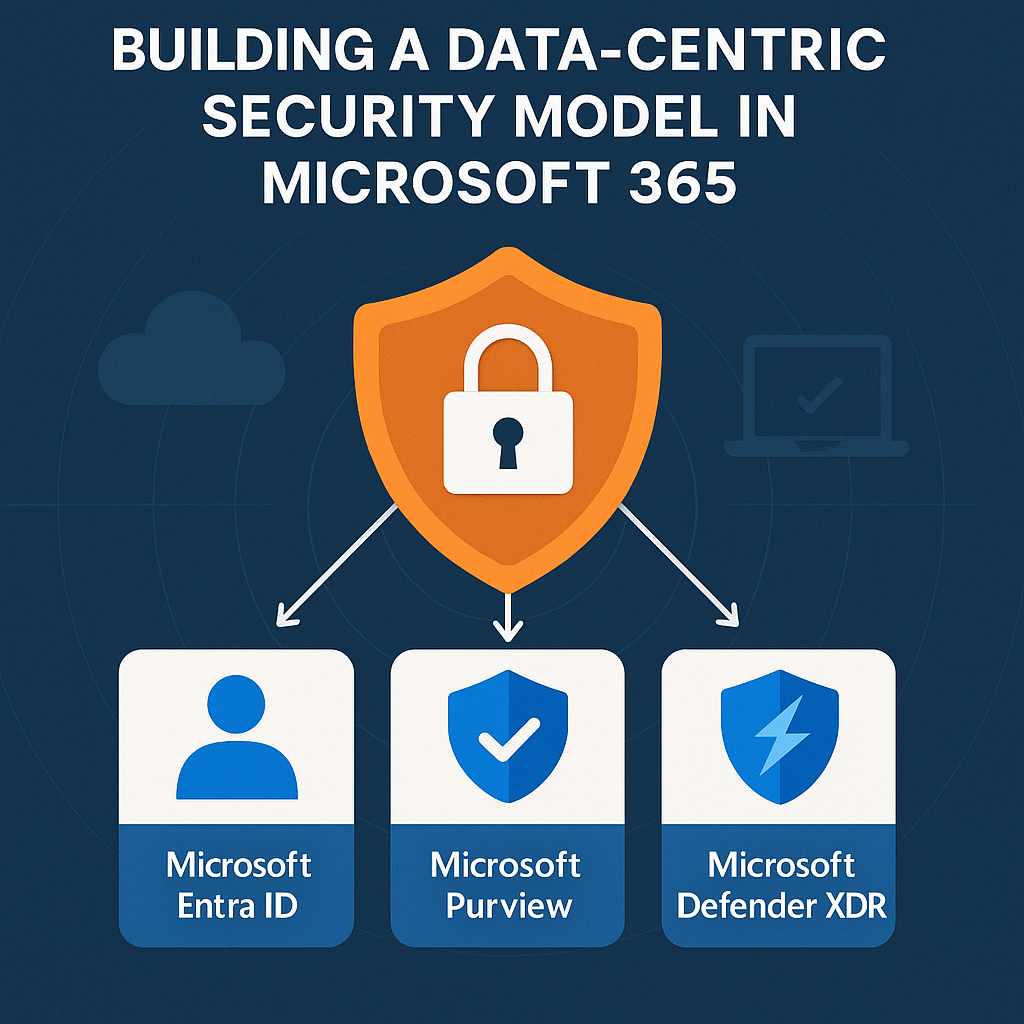
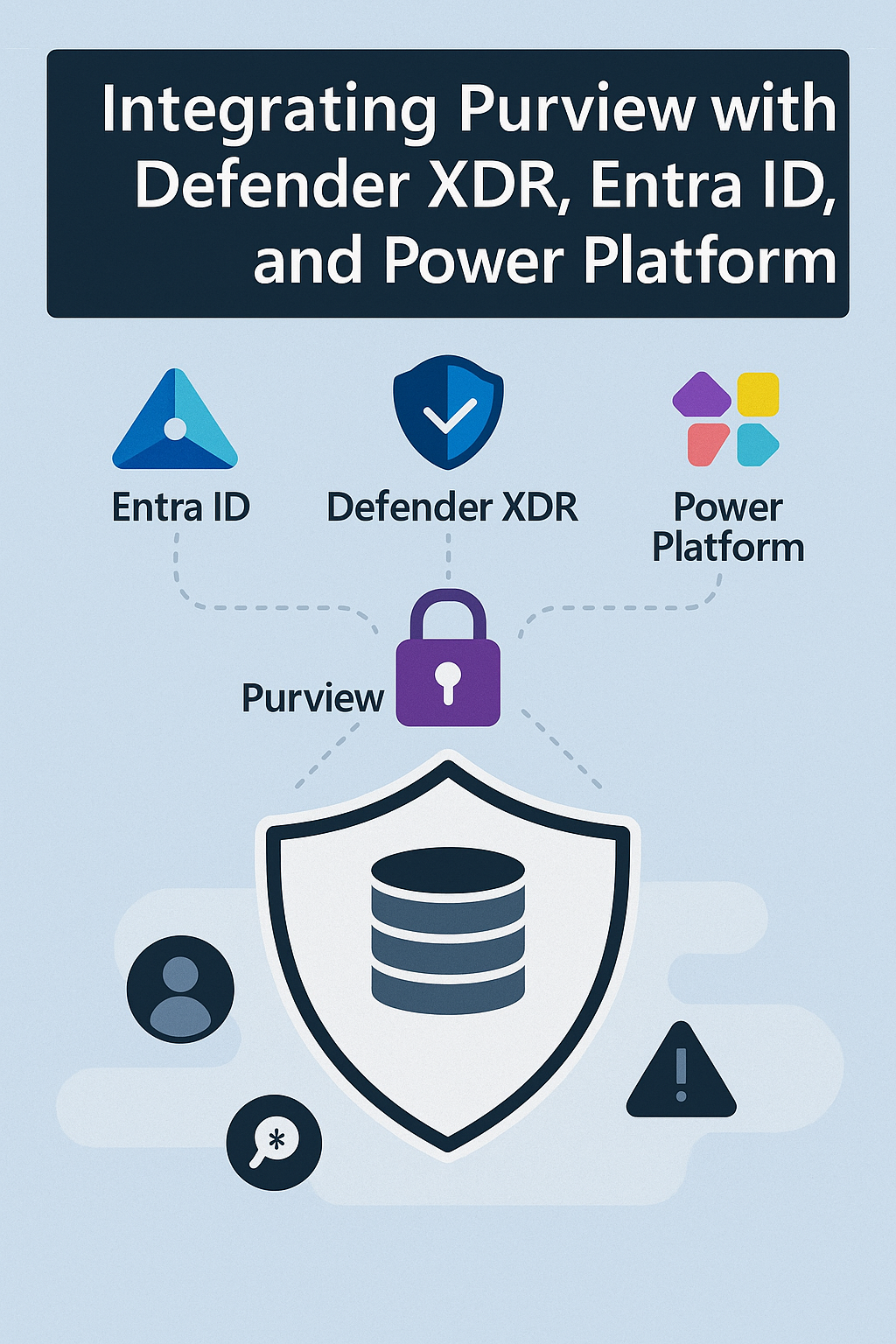
At the heart of this approach is Microsoft Purview, integrated with Microsoft Entra ID and Microsoft Defender XDR. Together, they create a security architecture where identity, device, and data protection work as one.
What Is Data-Centric Security?
A data-centric approach means security follows the information, not the infrastructure.
In practical terms, it focuses on:
- Understanding your data – Discover what sensitive information exists.
- Classifying and labeling – Define how it should be handled.
- Controlling access – Enforce who can use it, how, and where.
- Monitoring and responding – Track every interaction for misuse or risk.
Instead of locking down entire systems, we protect what truly matters , the data itself.
The Microsoft 365 Data-Centric Architecture
Microsoft 365’s data security model connects three major layers:
| Layer | Purpose | Technology Examples |
| Identity & Access | Verify who’s requesting access and enforce conditional access | Microsoft Entra ID, Conditional Access, Privileged Identity Management (PIM) |
| Data Classification & Protection | Discover, label, and protect sensitive content | Microsoft Purview Information Protection, Sensitivity Labels, Auto-Labeling |
| Threat Detection & Response | Detect, correlate, and act on suspicious activities | Microsoft Defender for Endpoint, Defender XDR, Insider Risk Management |
These layers communicate continuously , every access request, file label, or data movement generates a signal that Purview and Defender use to assess and mitigate risk.
The Role of Microsoft Entra ID
Microsoft Entra ID (formerly Azure AD) is the trust foundation of Purview.
It provides identity-based control that determines who can access data and under what conditions.
Key Entra capabilities in a Purview environment:
- Conditional Access: Grants or denies access to content based on context , device compliance, location, or risk level.
Example: Block downloading labeled “Highly Confidential” files on unmanaged devices.
- Privileged Identity Management (PIM): Controls elevated permissions, ensuring admin access is time-bound and auditable.
- Identity Protection: Detects risky sign-ins and compromised accounts that might try to access sensitive data.
When Purview applies encryption through sensitivity labels, the decryption rights come from Entra , ensuring access decisions are always identity-aware and dynamic.
The Role of Microsoft Defender XDR
While Entra authenticates and authorizes users, Microsoft Defender XDR ensures data protection continues after access is granted.
It correlates activity across endpoints, email, and cloud apps, detecting behaviors that Purview might flag as insider or DLP alerts.
Example:
- A user legitimately opens a confidential document (allowed by Entra).
- Moments later, Defender detects the same user uploading it to a personal cloud.
- This triggers a Purview DLP policy → warning or block action.
- If risky behavior continues, Adaptive Protection increases restrictions automatically.
Defender + Purview = continuous protection before, during, and after access.
How Purview Connects It All
Purview acts as the intelligence hub between identity and threat signals.
It collects telemetry from Entra (who accessed) and Defender (how it was used), then enforces rules such as:
- Applying encryption automatically when content matches sensitive information types
- Blocking uploads or copying of labeled data to unmanaged locations
- Triggering insider risk policies for anomalous download patterns
- Logging everything in Purview Audit (Premium) for forensics
This integration ensures that compliance and security policies speak the same language , labels, users, and alerts are unified across the ecosystem.
Real-World Example: HR Data in a Multi-Cloud Organization
Scenario:
Contoso’s HR department stores employee records in SharePoint, shares them through Teams, and integrates with Dynamics 365 and a third-party payroll app hosted on AWS.
Without data-centric security:
Each system applies its own access controls , inconsistent, hard to audit, and risky when data crosses clouds.
With Purview integration:
- HR records are automatically labeled Confidential–HR.
- Entra ID ensures only HR staff can decrypt files.
- DLP policies prevent uploading labeled data to external sites.
- Insider Risk Management monitors for mass downloads.
- Defender XDR correlates alerts across all systems.
Result: Data remains protected and traceable wherever it travels , even beyond Microsoft 365.
Designing a Data-Centric Security Model
To build your own model, start with these steps:
- Map your data flows: Identify where sensitive information lives and how it moves.
- Define sensitivity labels: Create clear tiers (e.g., Public → Confidential → Highly Confidential).
- Connect identity to data: Use Entra Conditional Access to enforce context-based protection.
- Extend to devices and clouds: Deploy Endpoint DLP and integrate non-Microsoft apps via Defender for Cloud Apps.
- Monitor and adapt: Use Insider Risk and Activity Explorer to fine-tune policies over time.
This layered approach ensures that every user action is evaluated through both a security and compliance lens.
Real-World Tip
Integrate before you automate.
Many organizations jump into auto-labeling and DLP policies too soon.
Instead, start by connecting Entra → Purview → Defender integrations first.
Once identity and telemetry are aligned, your automated protections will be accurate and sustainable.
Exam Tip (SC-401)
Expect questions that link data classification with identity and device conditions.
Example scenario:
“A user attempts to open a labeled document on an unmanaged device , what Purview + Entra feature prevents access?”
Answer: Conditional Access with sensitivity label encryption enforcement.
Conclusion
In a borderless world, the strongest defense is one built around the data itself.
Microsoft Purview, Entra, and Defender deliver a connected architecture that:
- Authenticates users intelligently,
- Protects information consistently, and
- Detects misuse instantly.
This is the essence of data-centric security , protection that lives with your data wherever it goes.
In the next article, PUR503 – Discover and Classify Data Automatically with Microsoft Purview, we’ll explore how Purview finds and categorizes sensitive data at scale using Sensitive Information Types, Exact Data Match, and Trainable Classifiers.
I am Yogeshkumar Patel, a Microsoft Certified Solution Architect and Enterprise Systems Manager with deep expertise across Dynamics 365 Finance & Supply Chain, Power Platform, Azure, and AI engineering. With over six years of experience, I have led enterprise-scale ERP implementations, AI-driven and agent-enabled automation initiatives, and secure cloud transformations that optimise business operations and decision-making. Holding a Master’s degree from the University of Bedfordshire, I specialise in integrating AI and agentic systems into core business processes streamlining supply chains, automating complex workflows, and enhancing insight-driven decisions through Power BI, orchestration frameworks, and governed AI architectures. Passionate about practical innovation and knowledge sharing, I created AIpowered365 to help businesses and professionals move beyond experimentation and adopt real-world, enterprise-ready AI and agent-driven solutions as part of their digital transformation journey. 📩 Let’s Connect: LinkedIn | Email 🚀














Post Comment