
PUR516 – Microsoft Purview: Real-World FAQs, Answers, and Expert Insights
Table of Contents
ToggleIntroduction
Over the past fifteen articles, we’ve explored Microsoft Purview from every angle , architecture, data protection, insider risk, lifecycle management, AI governance, and enterprise operations.
This final article answers the most common real-world and exam-level questions about Purview , the ones customers, architects, and security professionals ask most often when implementing or managing it.
If you master these, you’ll understand not just how Purview works, but why it’s the cornerstone of Microsoft’s data security strategy.
🔹 Section 1: Understanding Microsoft Purview Fundamentals
Q1: What exactly is Microsoft Purview?
Purview is Microsoft’s unified data security, compliance, and governance platform for Microsoft 365, Azure, multi-cloud, and on-premises environments.
It helps organizations:
- Discover and classify sensitive data.
- Protect information with labels and encryption.
- Prevent data loss and insider risks.
- Manage retention, auditing, and regulatory compliance.
- Govern AI data interactions (e.g., Microsoft 365 Copilot).
Q2: How is Purview different from Microsoft Defender or Entra ID?
- Entra ID (Azure AD): manages who can access resources.
- Defender XDR: detects and responds to threats.
- Purview: governs the data itself , where it lives, how it’s labeled, who uses it, and whether it stays compliant.
Together, they form a Zero Trust triad: Identity + Threat + Data.
Q3: What licenses include Purview features?
- Microsoft 365 E3: includes core labeling, DLP, and Audit (Standard).
- Microsoft 365 E5 / E5 Compliance: adds auto-labeling, Insider Risk, Audit (Premium), Adaptive Protection, and advanced DLP.
- Add-ons: allow 10-year audit retention and records management.
🔹 Section 2: Data Discovery and Classification
Q4: What is data classification and why does it matter?
Classification identifies which data is sensitive or regulated so policies can protect it automatically.
It’s the first step in any Purview deployment. Without it, labeling and DLP policies can’t act intelligently.
Q5: What are Sensitive Information Types (SITs)?
SITs are built-in detection patterns for structured data such as credit card numbers, national IDs, or tax references.
Purview includes 300+ pre-defined SITs, and you can create custom ones for business-specific data like employee IDs or contract codes.
Q6: How does Exact Data Match (EDM) improve accuracy?
EDM compares content to a securely hashed reference dataset (e.g., real customer records) for exact matches , reducing false positives when precision matters (e.g., healthcare or banking).
Q7: What are Trainable Classifiers?
AI-powered models trained on real documents that identify unstructured data such as contracts, HR reviews, or source code based on context, not keywords.
🔹 Section 3: Sensitivity Labels and Label Policies
Q8: What are Sensitivity Labels?
Labels classify and protect data by applying encryption, access restrictions, watermarks, and visual markings.
Protection stays with the file wherever it travels.
Q9: What’s the difference between a label and a label policy?
- Label: defines how content is protected.
- Label Policy: defines who can use the label, and where (files, emails, sites).
Q10: Can Sensitivity Labels protect Microsoft Teams and SharePoint sites?
Yes , container labels apply to Teams, Groups, and SharePoint sites, controlling guest access, sharing permissions, and privacy settings.
Q11: What happens if multiple labels apply?
The most restrictive label wins (e.g., “Highly Confidential” overrides “Internal”).
🔹 Section 4: Data Loss Prevention (DLP)
Q12: What does Purview DLP actually prevent?
It monitors and controls how users share or transfer sensitive data across:
- Exchange Online
- SharePoint and OneDrive
- Teams chat and meetings
- Endpoints (Windows/macOS)
- Cloud apps (via Defender for Cloud Apps)
It can warn, block, or log risky actions like external sharing, USB copies, or printing.
Q13: How do simulation and enforcement modes differ?
- Simulation mode: Logs and tests policies without blocking actions , ideal for tuning rules.
- Enforcement mode: Applies full policy actions (warn, block, override).
Always pilot in simulation mode first.
Q14: What’s Adaptive Protection in DLP?
Adaptive Protection links Insider Risk and DLP. It dynamically adjusts enforcement based on user risk level (Minor → Moderate → Elevated).
High-risk users get stricter DLP rules automatically.
Q15: How does Endpoint DLP extend protection?
Endpoint DLP applies DLP rules directly on devices , monitoring copy, print, upload, and Bluetooth actions even when offline.
🔹 Section 5: Insider Risk Management and Adaptive Protection
Q16: How does Insider Risk Management differ from DLP?
DLP focuses on data actions (what happened).
Insider Risk focuses on user behavior (why it happened).
It analyzes signals like mass downloads, HR events, or security violations to detect risky patterns before data loss occurs.
Q17: How does Purview protect privacy during Insider Risk investigations?
By default, users are anonymized.
Only authorized investigators can unmask identities when alerts are validated.
All actions are audited, ensuring ethical oversight.
Q18: How does Adaptive Protection link IRM and DLP?
Adaptive Protection automatically changes DLP enforcement based on risk signals from Insider Risk.
If a user’s behavior becomes suspicious, stricter rules apply instantly , no manual admin change required.
🔹 Section 6: Lifecycle Management and Records
Q19: What’s the difference between Retention Policies and Retention Labels?
- Retention Policies: apply broadly (e.g., all mailboxes).
- Retention Labels: apply granularly (specific files or folders) and can declare official records.
Q20: What is event-based retention?
Allows retention to start based on a business event (e.g., “7 years after employee termination”) rather than file creation date.
Q21: What is a Disposition Review?
An approval workflow at the end of a retention period that lets reviewers confirm whether to delete, extend, or retain data , ensuring defensible deletion.
🔹 Section 7: Auditing and Monitoring
Q22: What does Microsoft Purview Audit capture?
User and admin activities across Microsoft 365 , from file access to label changes and Copilot interactions.
Audit (Premium) adds intelligent insights, extended retention (up to 10 years), and higher API bandwidth.
Q23: Is auditing on by default?
Yes , Audit (Standard) is enabled automatically. You can verify via PowerShell:
Get-AdminAuditLogConfig | Format-List UnifiedAuditLogIngestionEnabled
Q24: Does Purview audit AI tools like Microsoft 365 Copilot?
Yes , Copilot events such as CopilotInteraction and CopilotDataAccessed are logged for governance and compliance tracking.
🔹 Section 8: Smart Compliance and Reporting
Q25: What’s the difference between Content Explorer and Activity Explorer?
- Content Explorer: shows what data is sensitive and where it’s stored.
- Activity Explorer: shows what users do with that data (access, copy, print, label change).
Q26: What is Compliance Manager used for?
It measures your organization’s compliance against frameworks (GDPR, ISO, NIST, HIPAA), assigns scores, and recommends improvement actions , like an internal compliance dashboard.
Q27: Can these tools integrate with Power BI or Security Copilot?
Yes. Both Explorer data and Audit logs can feed into Power BI for visual analytics, and Security Copilot can summarize trends and suggest policy optimizations using natural language prompts.
🔹 Section 9: AI and Copilot Governance
Q28: How does Purview secure Microsoft 365 Copilot?
Purview applies the same labeling, encryption, DLP, and audit controls to AI-accessed data.
Copilot only accesses data the user already has permission for , governed by Entra ID and Purview.
Q29: How does DLP protect against sensitive AI prompts?
DLP policies inspect text entered into Copilot. If sensitive data (e.g., credit card numbers) is detected, the action can be blocked or logged.
Q30: Does Copilot train on my company data?
No. Copilot uses Microsoft’s secure LLMs and doesn’t train the model on your tenant’s data. Your content remains within your compliance boundary.
🔹 Section 10: Integration Across Microsoft Security
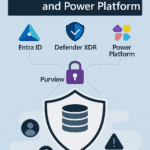
Q31: How do Purview, Entra ID, and Defender XDR work together?
- Entra ID authenticates and enforces Conditional Access.
- Purview governs and labels data.
- Defender XDR detects threats and correlates incidents.
Together, they deliver unified, risk-based protection across identity, device, and data layers.
Q32: How is Power Platform data protected?
Purview and Power Platform DLP policies restrict which connectors can exchange data.
Power BI inherits sensitivity labels from source datasets, ensuring consistent protection.
Q33: Can Purview integrate with SIEMs or third-party tools?
Yes , through the Office 365 Management Activity API or Microsoft Sentinel connector, allowing external monitoring and incident correlation.
🔹 Section 11: Operational Governance
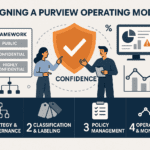
Q34: How should organizations structure a Purview operating model?
Include clear roles:
- Executive Sponsor for strategy and funding.
- DPO or Compliance Officer for regulatory oversight.
- Program Manager for cross-functional coordination.
- Admins and Data Owners for implementation and review.
- End Users for daily labeling and data handling.
Establish governance pillars: Strategy, Classification, Policy, Operations, and Improvement.
Q35: What metrics demonstrate Purview success?
| Metric | Goal |
| % of data labeled | >80% |
| DLP false positives | <10% |
| Incident resolution time | <24 hours |
| Policy review completion | 100% quarterly |
| Training completion | >95% of staff |
These KPIs show measurable business value and compliance maturity.
Q36: How often should Purview policies be reviewed?
Quarterly at minimum , and immediately after major organizational or regulatory changes.
Automate review reminders using Compliance Manager improvement actions.
🔹 Section 12: Common Pitfalls and Expert Tips
Q37: What are the top 3 Purview deployment mistakes?
- Deploying labels before defining a classification framework.
- Enforcing DLP too early, causing user frustration.
- Not aligning labels and permissions with Entra security groups.
Q38: What’s the best rollout sequence for new organizations?
- Discover and classify data.
- Define label taxonomy.
- Publish labels to pilot groups.
- Configure DLP and retention policies.
- Integrate Insider Risk and Adaptive Protection.
- Monitor via Audit and Explorers.
Q39: How can organizations build user adoption?
- Communicate early and clearly.
- Use policy tips to teach, not block.
- Recognize compliance as part of performance culture.
- Include data handling in onboarding and annual training.
Q40: How does Purview handle multi-cloud and on-premises data?
Via the Purview Data Map and Scanner, which classify and label data across Azure, AWS, SQL, and file shares , providing a unified compliance view.
🔹 Section 13: Exam and Implementation Insights
Q41: For SC-401 exam readiness, which areas should I master?
- Sensitivity labels and label policies
- DLP and Endpoint DLP configuration
- Insider Risk and Adaptive Protection
- Retention and Records Management
- Audit (Standard vs Premium)
- Purview + Defender + Entra integration
- Purview governance roles and metrics
Q42: What real-world scenarios often appear in SC-401 exams?
- Auto-labeling sensitive data based on patterns
- Restricting access to encrypted files
- Investigating DLP violations using Audit logs
- Applying retention labels to regulated content
- Blocking exfiltration via Endpoint DLP
- Linking Insider Risk signals to Adaptive Protection
🔹 Section 14: The Future of Microsoft Purview
Q43: What’s next for Purview?
- Data Security Posture Management (DSPM): holistic visibility into where sensitive data resides and who accesses it.
- AI-driven compliance insights: predictive alerts via Security Copilot.
- Cross-platform governance: expanding beyond Microsoft 365 to more SaaS and multi-cloud integrations.
Purview is evolving from a compliance suite into a data intelligence and risk orchestration platform.
Conclusion
From discovering data to auditing AI interactions, Microsoft Purview provides a single, unified governance fabric that protects information wherever it travels.
By combining identity, data, and threat intelligence across Entra ID, Defender XDR, and the Power Platform, it transforms compliance into continuous assurance.
Whether you’re preparing for SC-401 certification or building an enterprise governance program, remember:
Purview is not just about compliance , it’s about confidence.
✅ End of Microsoft Purview Master Series (PUR501–PUR516)
Congratulations , you now have a complete, enterprise-grade understanding of Microsoft Purview’s architecture, security, compliance, and operational best practices.
I am Yogeshkumar Patel, a Microsoft Certified Solution Architect and Enterprise Systems Manager with deep expertise across Dynamics 365 Finance & Supply Chain, Power Platform, Azure, and AI engineering. With over six years of experience, I have led enterprise-scale ERP implementations, AI-driven and agent-enabled automation initiatives, and secure cloud transformations that optimise business operations and decision-making. Holding a Master’s degree from the University of Bedfordshire, I specialise in integrating AI and agentic systems into core business processes streamlining supply chains, automating complex workflows, and enhancing insight-driven decisions through Power BI, orchestration frameworks, and governed AI architectures. Passionate about practical innovation and knowledge sharing, I created AIpowered365 to help businesses and professionals move beyond experimentation and adopt real-world, enterprise-ready AI and agent-driven solutions as part of their digital transformation journey. 📩 Let’s Connect: LinkedIn | Email 🚀















Post Comment